AWS Load Balancer Comparison: Choosing the Right Tool for the Job
Working through AWS Solutions Architect Associate prep has been surprisingly rewarding. While I often take load balancers for granted in my SRE work, diving deeper into the architectural patterns and trade-offs has sharpened my understanding of nuances I knew existed but never really examined closely.
Turns out mapping each load balancer type against real-world use cases makes the Well-Architected Framework principles much more concrete. It’s fascinating how studying for certifications—even covering familiar territory—forces you to articulate the reasoning behind what might seem like routine choices.
The Four Types: When to Use What
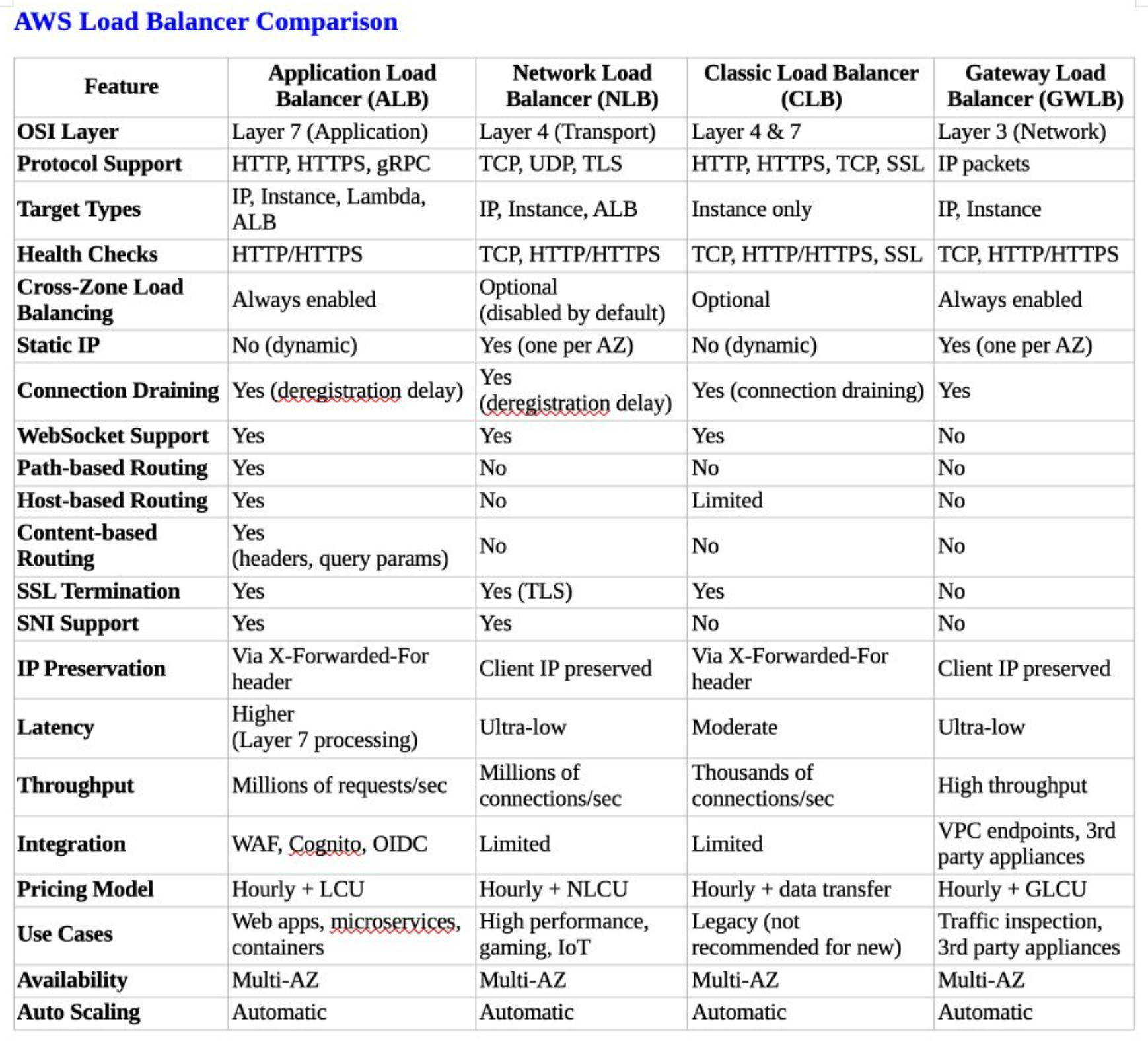
Application Load Balancer (ALB)
Layer 7 HTTP/HTTPS routing with intelligence
ALB operates at the application layer, providing advanced routing based on HTTP headers, paths, and query parameters. This makes it optimal for containerized applications, microservices, and scenarios requiring integration with AWS services like WAF, Cognito, or Lambda functions.
Best for: Content-based routing, microservices architectures, anything needing precise traffic distribution across multiple application versions.
Network Load Balancer (NLB)
Layer 4 performance powerhouse
NLB functions at the transport layer, delivering ultra-low latency and high throughput performance. Essential for applications requiring static IP addresses, maximum performance, or non-HTTP protocols like TCP, UDP, or TLS.
Best for: Gaming platforms, IoT workloads, high-frequency trading systems, or anything where preserving client IP addresses matters.
Classic Load Balancer (CLB)
The legacy option
First-generation load balancer supporting both Layer 4 and Layer 7 operations. While functional, it lacks the advanced capabilities of newer options. AWS documentation recommends migration to ALB or NLB for enhanced features and improved cost efficiency.
Best for: Legacy applications that haven’t migrated yet. Seriously, migrate when you can.
Gateway Load Balancer (GWLB)
Layer 3 security inspection
GWLB operates at the network layer, enabling transparent traffic inspection through third-party security appliances. Allows deployment of virtual firewalls, intrusion detection systems, and deep packet inspection tools without altering existing network architecture.
Best for: Environments requiring complete security analysis, compliance-heavy industries, or anywhere you need to insert security appliances transparently.
The Real Learning
What struck me most during this study wasn’t just the technical differences—it was how these choices cascade through your entire architecture. Pick the wrong load balancer type, and you might find yourself working around limitations that could have been avoided with better upfront planning.
The certification prep forced me to think beyond “this works” to “this is the right tool for this specific job.” That kind of intentional architecture thinking definitely carries over into day-to-day work.
Quick Reference Summary
Sometimes the most valuable learning comes from revisiting the fundamentals with fresh eyes. Even familiar tools have nuances worth understanding deeply.